
Vulnerability Assessment
Vulnerability Assessment
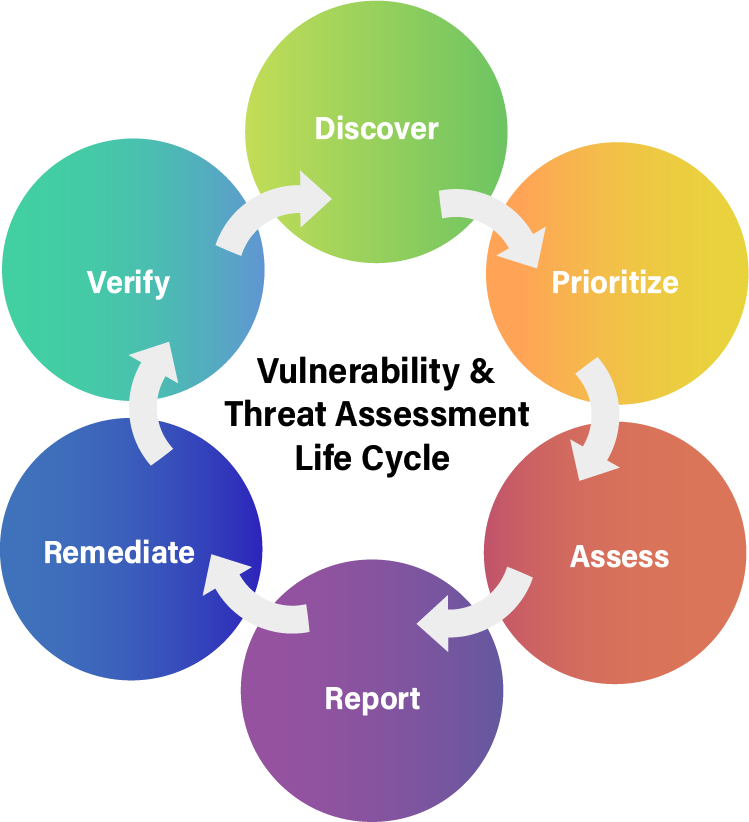
At Redkite Network, we recognize that staying ahead of cyber threats requires a proactive approach. Our comprehensive vulnerability assessment services are designed to identify weaknesses in your digital infrastructure, enabling you to strengthen your security posture and mitigate potential risks effectively.
What is a Vulnerability Assessment?
A vulnerability assessment is a systematic review of your IT systems, networks, and applications to uncover potential weaknesses that could be exploited by cyber attackers. Unlike penetration testing, which simulates real-world attacks, vulnerability assessments focus on identifying vulnerabilities before they can be exploited, allowing you to take preemptive action to address them.
Why Choose Redkite Network?
Expert Analysis: Our team of cybersecurity experts possesses deep knowledge and experience in identifying vulnerabilities across various digital environments. We utilize industry-leading tools and methodologies to conduct thorough assessments tailored to your specific requirements.
Comprehensive Coverage: From network infrastructure to web applications and beyond, our vulnerability assessment services cover all aspects of your digital ecosystem. Whether you're concerned about software vulnerabilities, misconfigurations, or insecure network protocols, we've got you covered.
Actionable Insights: We go beyond merely identifying vulnerabilities; we provide actionable insights and recommendations to help you remediate them effectively. Our detailed reports highlight priority issues and provide guidance on implementing security best practices to strengthen your defenses.
Timely Assessments: In today's fast-paced digital landscape, timely vulnerability assessments are essential. Our efficient assessment process ensures quick turnaround times without compromising the quality or depth of our analysis, allowing you to address vulnerabilities promptly.
Customized Solutions: We understand that every organization is unique, with its own set of challenges and requirements. That's why we tailor our vulnerability assessment services to suit your specific needs, providing personalized solutions that address your most pressing security concerns.
Our Vulnerability Assessment Services Include:
Network Vulnerability Scanning
Web Application Security Testing
Cloud Infrastructure Assessments
Mobile Device Security Assessments
Configuration Reviews
Compliance Audits
Secure Your Digital Assets with Redkite Network
Don't leave your organization vulnerable to cyber threats. Take proactive steps to identify and address vulnerabilities with Redkite Network's comprehensive vulnerability assessment services. Contact us today to schedule a consultation and take the first step towards a more secure future.
