
Cyber Security
Cyber Security
Cyber security refers to a set of techniques used to protect the integrity of networks, programs, and data from attack, damage, or unauthorized access.
Cybersecurity refers to the practice of protecting electronic devices, networks, and sensitive information from unauthorized access, theft, damage, or disruption. With the increasing use of the internet, social media, and other digital technologies, cybersecurity has become a critical concern for individuals, businesses, and governments alike.
From a computing point of view, security comprises cyber security and physical security — both are used by enterprises to protect against unauthorized access to data centers and other computerized systems. Information security, which is designed to maintain the confidentiality, integrity, and availability of data, is a subset of cyber security. The use of cyber security can help prevent cyber attacks, data breaches, and identity theft and can aid in risk management.
Given the constantly evolving nature of cyber threats, cybersecurity experts must continuously monitor and update their defenses to stay ahead of potential attacks. This often involves conducting regular vulnerability assessments and penetration testing to identify and address any weaknesses in a system's security. Additionally, individuals and organizations must be vigilant about practicing good cybersecurity habits, such as creating strong passwords, avoiding suspicious emails or links, and keeping software up-to-date.
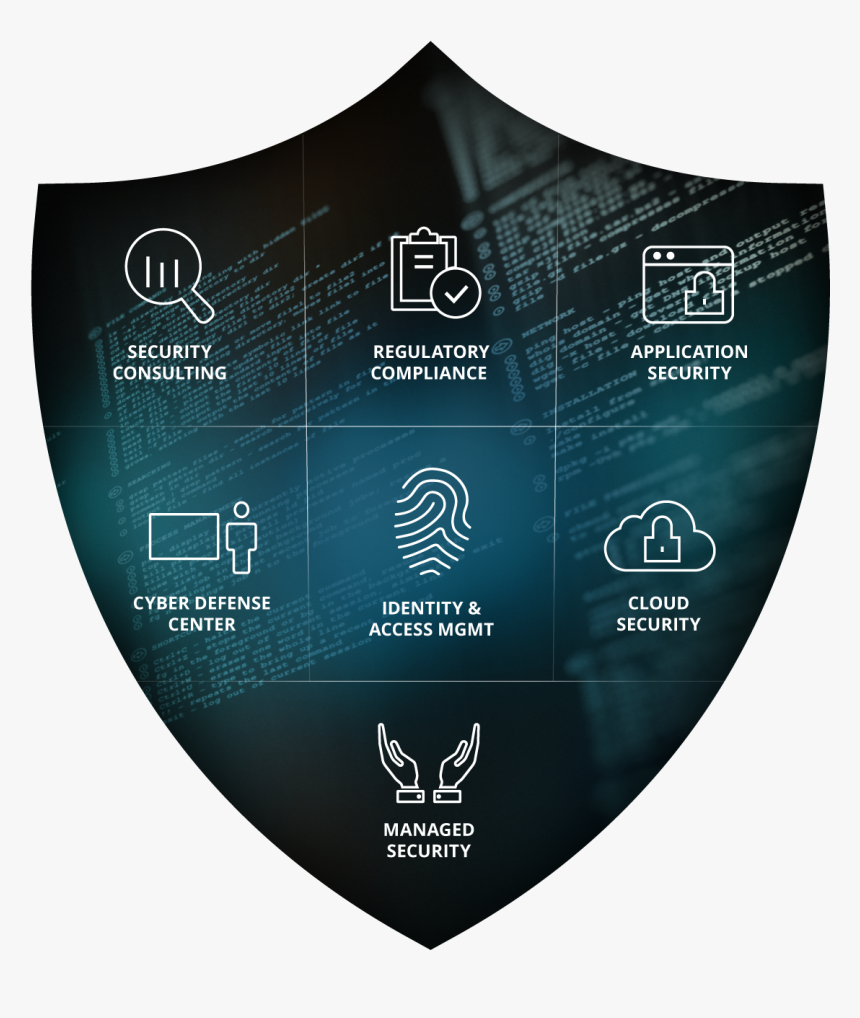
Redkite Network offers some cybersecuirty services:
SOC as Service
Incident Response
Threat Management and Defense
Network Security
