
Penetration Testing
Penetration Testing
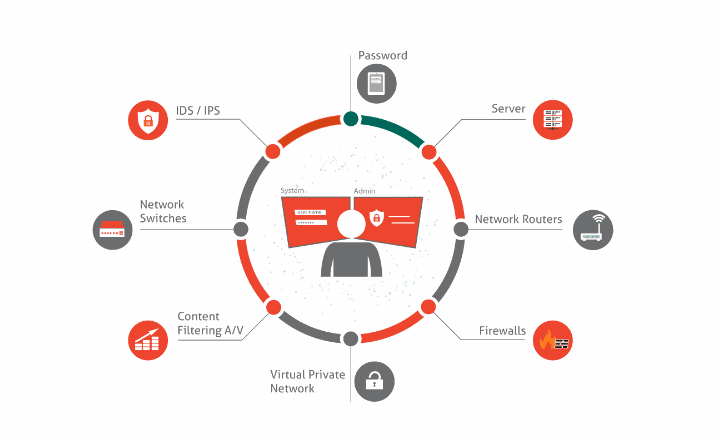
At Redkite Network, we understand that safeguarding your digital assets is paramount in today's interconnected world. Our penetration testing services are designed to identify vulnerabilities within your systems, networks, and applications, empowering you to proactively defend against potential cyber threats.
What is Penetration Testing?
Penetration testing, often referred to as pen testing, is a systematic approach to evaluating the security of your IT infrastructure. It involves simulated cyber-attacks carried out by skilled professionals to uncover weaknesses that malicious actors could exploit. By emulating the tactics of real-world attackers, we provide valuable insights into your organization's security posture, helping you mitigate risks effectively.
Why Choose Redkite Network?
Expertise: Our team comprises certified ethical hackers with extensive experience in cybersecurity. They possess the knowledge and skills necessary to identify and address even the most sophisticated security vulnerabilities.
Comprehensive Approach: We offer a range of penetration testing services tailored to meet your specific needs. Whether you require external assessments, internal evaluations, web application testing, or wireless network assessments, we've got you covered.
Thorough Analysis: Our testing methodologies go beyond surface-level scans. We delve deep into your systems, employing advanced techniques to uncover hidden vulnerabilities that automated tools may overlook.
Actionable Insights: We provide detailed reports outlining our findings, along with actionable recommendations to strengthen your security defenses. Our goal is not just to identify weaknesses but also to empower you with the knowledge needed to address them effectively.
Client-Centric Approach: We prioritize clear communication and transparency throughout the testing process. Our team works closely with you to understand your unique requirements and tailor our approach accordingly.
Our Penetration Testing Services Include:
External Network Penetration Testing
Internal Network Penetration Testing
Web Application Penetration Testing
Wireless Network Penetration Testing
Social Engineering Assessments
Mobile Application Penetration Testing
Cloud Infrastructure Assessments
Protect Your Assets with Redkite Network
Don't wait until it's too late. Take proactive steps to safeguard your organization's sensitive data and infrastructure with Redkite Network's penetration testing services. Contact us today to schedule a consultation and take the first step towards a more secure future.
